Great – you’re still at it: you’ve dealt with the importance of information security and set up an organization for it. Now let’s start with one of the most important components, the risk management system.
The first step in the implementation process is to take stock of your information. More on this in a moment. You can assign the task to your newly created organization and then have it report back to you.
Risk management terms briefly explained
While you have given this task to the organization, we would like to explain some risk management terms to you, because you will be confronted with them in the course of further development and you will be making decisions about them. It’s about risk, how to make it measurable and how you deal with it strategically:
- Risk capacity: This is the maximum impact of an emerging risk on your company that the company can just about bear without jeopardizing its existence.
- Risk appetite: These are risks that a company must and wants to take as part of its strategy. You can also simply say that no company can be successful without taking risks. You should be aware of these.
- Risk tolerance: This is the expression of the fluctuation range around the risk appetite that a company is willing to take
- Residual risk: In the real world, nothing is without risk. Of course a meteorite can fall on your data center! The risk is small, but not zero!
These indicators or key figures are important for the risk assessment in the following steps. This is because you will have to decide how to deal with identified risks. The figures mentioned above will help you to classify them.
Now it’s time to get started with the inventory.
For the information inventory, it is best to start with the business processes and define what, where and how is processed, generated and stored.
The “where” should also include organizational and spatial details. The “how” should also include the communication structure and you can summarize the “what” if you can be sure that risks have the same effect on a group of information (e.g. everything in a HIS system). You can also use your existing data protection procedure directory as a source of knowledge for these considerations.
At this point, you have defined the context according to ISO/EC 27005 and set the starting point for risk identification, completed the modeling of the context according to the MONARC method, defined the conceptual model of the governance framework in COBIT and fulfilled at least 18 essential MUST items according to the B3S for hospitals. You and your employees are well on your way!
Risk management starts after the inventory has been created
Once you have created your inventory, you can start to delve deeper into risk management. First, consider the value of the information for your company. Take strategic, economic, legal and medical perspectives into account. For example, what are the consequences of
- a lack of access to the information asset (e.g. network disruption, environmental disaster, encryption),
- an intentional (forgery) or unintentional change (transfer by a restore process carried out incorrectly in the production system),
- theft, whether physical or digital,
- disclosure to unauthorized third parties (e.g. sale of used IT with improperly erased data carriers)?
In this context, we refer to direct and indirect consequences, i.e. disruptions in billing, penalties due to a data protection breach, loss of reputation due to negative press, harm to patients and so on.
From this information you derive the value and criticality of the information asset, and yes, the resulting valuation will usually be an assessment.
In the next step, you look at the risks from two perspectives
- The probability of occurrence, expressed for example by the question “How often does this happen (to us; in my industry)”
- The extent of the impact of the risk occurrence
An overall assessment can be derived from the variables, which is used as a parameter with others to map your risk landscape. Too complicated? So let’s take an example.
If the interface between your HIS and the administration system fails, you cannot issue invoices. The interface is not particularly stable, runs under an account whose password is only known to the two IT employees and fails once a week. They are a bit older and also fail more often. If the two events coincide, the billing stops until one of them is back. This could look like this in your risk management system:
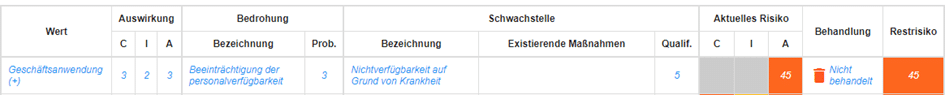
The actual (or residual) risk of 45 results from the impact 3) for the factor “Availability” (column A=Availability), the probability of occurrence 3 (can occur occasionally) and the qualification 5 (nothing done yet).
A risk matrix helps with the decision
All of this results in your risk matrix, which you then use to decide how to deal with the risks, taking into account your risk capacity, appetite and tolerance:
- Avoid – you stop the risky activity
- Reduce – you take measures to reduce the risk
- Accept – you do nothing, it makes no economic sense either to avoid the risk or to reduce it
- Transfer – you transfer the risk to someone else, for example by taking out insurance
And when you’ve done all that…
…start again from the beginning.
But first, let’s take a look at what to do in the next blog post if the worst comes to the worst !
Cyber risk check – a new service from Oberender AG
Do you want to know where you stand in terms of information security right now? Great – then let’s do the cyber risk check together. You can find more information here.





